Read about two fundamental types of GDPR audits: for company and for applications. These are two complementary and necessary verifications that are worth introducing in business.
From the article you will learn:
- about the differences between the GDPR audit of the organization and application;
- the most important steps during the audit;
- what questions the audits answer and what knowledge you can get from them.
Verification of the security of organizations or systems are complex processes that require work and time. All you need to know here that there are about two fundamental types of GDPR audits: for company and for applications. Learn about the differences and why business resources should be secured in these times.
It might be quite confusing what is the difference between these two: Organization GDPR Audit vs Application GDPR Audit. Many specialists DO NOT know the key differences and use these terms interchangeably or incorrectly. Here at Lemlock there were several times of explaining this difference during application security verification and application GDPR checks for various web and mobile systems. We always try to resolve any doubts in what is it audit and whether should it be taken into account because in many cases both audits are necessary there are many differences in the audit scopes of both audits, and the companies are not aware of it.
Differences between Organization GDPR Audit vs Application GDPR Audit
The best way to picturize the confusion in IT auditing is when Lemlock team had a conversation with a Client once and we have asked if the application was checked in terms of GDPR. The Client claimed that it was confirmed by lawyers. We were wondering how lawyers can verify GDPR compliance of the IT system without deep understanding of IT system architecture, databases, programming languages or server configurations. It was obvious for us that lawyers would have analysed the outcome of such audit however not necessary be able to prepare one. In that moment we realized that Client had in mind the preparation of the organization to be compliant with GDPR and not about technical verification of the IT application. The most important differences between the aforementioned and obligatory audits for business will be explained below.
GDPR compliance of the organization
Such audit and audit steps are usually either specific verification for the organization in terms of the GDPR or it can be a part of the larger Data Governance process. Such audit helps to answer the following questions:
- Is my company able to manage the data protection of my clients, employees, and subcontractors?
- Where can I store personal data in digital (e.g. systems, databases) and analogue (e.g. paper documentation) form?
- Is there any risk in my organization as part of the processing of personal data?
- Do I have to prepare internal procedures/processes (security policies) that my employees must follow to reduce the risk?
- Do my employees require additional training to understand how to deal with personal data?
- Do I need a Data Protection Officer in my organization and what will be his/her duties?
The audit may include Data audit and it can involve analysis of the organization's assets in terms of the requirements specified by GDPR. Then recording of organizational processes related to the processing of personal data and recording of digital assets. Interviews with employees should be conducted to extend previous recordings to more accurate information on digital assets. It is also important to create Data Protection Impact Assessment, DPIA (if necessary). And last but not least conducting Risk analysis and preparation of documents required by GDPR and Risk management activities - procedures, recommendations, security policies.
Technical GDPR audit for application
In the case of this verification and audit steps, we focus on other areas as part of the application control, and the audit allows us to answer such questions as:
- How does my web/mobile/IoT application process personal data?
- Does the system architecture of my IT platform meet the principle of Privacy by Design?
- Does the domain model (database structure) of my application allow me to handle GDPR provisions (ie the Right to be forgotten, Right to rectification, etc)?
- How does the source code of the application deal with personal data?
- Does my system import / export personal data from / to other systems, and if so, how does it support data management and consent management between data processors and data controllers?
- Does the API interface of my application correctly adress the Privacy by default principle?
- How does my application support user consents, especially if consent is changed?
- Are there any system vulnerabilities that can compromise the privacy of my users?
- How are personal data stored as private (are there multi storage, data minimization, encryption, etc.)?
- What is my data backup policy and how does it relate to GDPR provisions?
- What does my server configuration and system logs look like regarding the GDPR requirements?
There are several permanent steps that should be included in the application GDPR-compliance audit. First of all, verification of the system's API in terms of UI and security by default. You must identify the data for which the system is a controller or processor. Then it is necessary to analyze the domain model security mechanism in regards to data protection by design. You also need to remember about the analysis of the system architecture in regards to profiling process. Next step is to verify the system architecture in regards to data subject provisions. The key action is to analyze the source code of consent management system and checking on how the system informs data processors when the user consents change. It is worth emphasizing here that when the application is constantly developed, it is necessary to take into account the process of Continuous Pentesting. Thanks to this, you can always be sure that regardless of the level of application development, it does not endanger business or its users.
Below you can find a quick comparison of both audits and activities that answers the question “what do auditors do” during such verification:
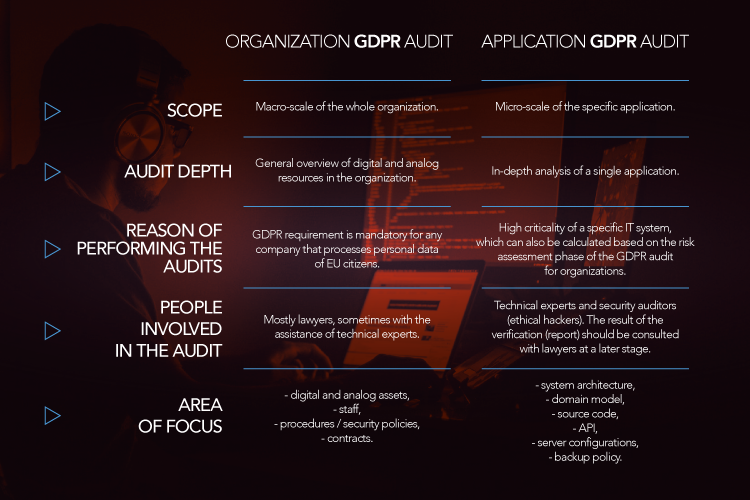
We hope that it is now more clear to you what the difference between these two audits is. If you would like to find out what the result of the GDPR technical audit for the application looks like, please contact us and we will provide you with an example report.








Let's stay in contact