Stop once and for all with theoretical talk about security of company or IT system. Turn it all into real action! Unauthorized violation of the web application and data breach cause many problems, however, all this can be easily avoided. Check out 5 ways to protect your application against hacker attacks.
From the article you will learn:
- what web applications are and what their specificity is;
- why web applications are hacked;
- what the types of attacks on Internet applications are;
- how to avoid cyberattack thanks to popular cybersecurity techniques.
We are happy to use web applications and share information, preferences, experiences, etc. Every day, millions of people log on to web applications, leaving personal or sensitive data, and other information that indicates an individual and specific person.
Everything happens somewhat naturally. Because being online and making various transactions this way is part of our day. We feel so at ease, and this great feeling of having a control over many aspects of our lives thanks to digital product... Until we notice that the application, which we like and trust so much, has been violated by an unauthorized person and our data (e.g. customer or partner data) has been manipulated or stolen. Then there is a panic among users, and companies bring a state of crisis.
Therefore, do not quietly count that "nothing bad will happen to our company, especially a hacker attack". Cybersecurity experts encourage adopting the business attitude in which we prevent and reduce the chances of infiltration.
What are web applications?
Web applications, also known as internet applications, are still one of the more eagerly chosen IT solutions for business and for cooperation models B2B (e.g. order systems, logistics systems), B2C (e.g. online stores, price comparison websites, offers websites) and C2C ( e.g. internet forums, social networking sites).
The web application works by running it in a web browser (so it requires constant access to the Internet and does not require installation), working on a server and communicating with the computer user's host. What may indicate that we are dealing with a web app is the login panel, so popular websites like Slack, Yahoo, Facebook are classified as web applications.
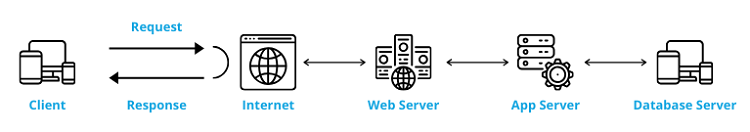
An important feature from the user's perspective that web applications should have is their flexibility and responsiveness. Thanks to this, apps have the ability to adapt to the size of the screen or the type of device currently used by the user. It positively affects the Customer Experience. The apps are universal in relation to the operating system and they can work on any system (e.g. MacOS or Windows).
Numerous web technologies are used to create applications, but the most commonly used are:
- Node.js,
- Django,
- PHP,
- Ruby on Rails,
- ASP.NET,
- AngularJS,
- Vue,js,
- React.
When making a choice in technology or in the way of developing an application, it is recommended to consult a Technology Partner or another entity specializing in the development of digital products.
Why do hackers attack web applications?
There are so many IT solutions and valuable online resources that are attractive to cybercriminals. So why are hackers so eager to perform attacks on web applications? From the observations of cybersecurity specialists, they do this to:
- gain access to the application, its architecture/infrastructure and databases,
- take control of the application, and then do the same with the server operating system,
- take over information left by users, e.g. personal/sensitive data, information related to payments,
- increase the range of their attack by introducing malware into the app. This makes it possible to carry out a collective infection (thanks to the Watering Hole attack technique) and quickly reach a larger number of users who then become the victims of the attack.
The aim of a hacker attack can be any private/public organization; small, medium and large companies. Common attack objects include government applications and websites belonging to state authorities. This is closely related not only to the desire to take control of servers, but also to gaining access to valuable information in databases (e.g. citizens' data or specific government representatives). In addition, according to the MMC report, companies representing the medical industry, trade, production or finance should feel at risk. Still don't believe you can be targeted? See in real time how many hacker attacks are carried out every second. Your company can be such a point on the map.
Types of attacks on web applications
There are three most common attacks on web applications, which account for about 50% of all identified attacks, and these are SQL Injection, Path Traversal, and Cross-Site Scripting (XSS). From the attacker's point of view, mentioned cyber threats are very effective and can quickly bring the desired benefits. Lemlock experts' admitted that many of the analyzed web applications:
- does not implement a responsible approach to application security attributes, i.e. confidentiality, integrity and availability of resources and information,
- do not meet security standards (e.g. OWASP, ASVS) in terms of architecture and infrastructure, as well as global requirements of GDPR or ISO 2700x,
- have critical code errors, including poorly secured access to the source code,
- are characterized by incorrect configuration, weak and incorrectly stored passwords, default settings,
- do not have adequate security measures against obtaining unauthorized access and control,
- are not resistant to injecting malicious code.
This contributes to the creation of slightly unpleasant statistics - about 70% of apps checked by us were sensitive to XSS attacks. It is worth knowing that even novice hackers are able to carry out these attacks without much effort, e.g. using open source software, often introducing automation.
How to prevent a cyber attack on the application?
No company can feel safe in a digital space where there are numerous threats that are not always obvious and visible with the naked eye. You need to be watchful, but above all always be one step ahead of the hackers. For this, you should introduce appropriate and multi-level security measures into the company's structures and IT solutions, including web apps. Here are 5 web application security best practices that can truly support you:
1) Security audit and penetration tests
Conducting the web application security audit involves undertaking controlled attacks on the application to check if its architecture, infrastructure and data are secure. These are some kind of simulations of real attacks performed by cyber criminals. Such audits and network penetration tests (white box, black box) are used to identify evident irregularities and hidden ones.
The expert at the time of auditing the application has one goal - to find all dangerous vulnerabilities. Hence, a sequence of actions is carried out, taking into account both the individual vulnerabilities and their connections, which in the future can be used to attack.
2) GDPR application audit
Ensuring compliance of the application with the requirements of the GDPR, i.e. the General Data Protection Regulation and other European Union regulations in the field of data protection and privacy of citizens.
The purpose of the application GDPR audit is, e.g., to provide recommendations regarding detected vulnerabilities that may affect data loss, violation or theft. Verifying the application in terms of compliance with basic rights (e.g. the right to access data, to be forgotten, to transfer data or to limit information processing), as well as principles (privacy by design, privacy by default).
3) Passive and active online scans
Launching the external vulnerability scan of a web application in a passive or active version. Scans differ primarily in scanning areas and depth. Such a security scanning allows quick and multi-level identification of vulnerabilities, which are critical from the point of view of business, application, and user.
At the end of the security scan, you get a report with ready for implementation recommendations. The scan is carried out automatically and in complete isolation (scans do not share any resources).
4) Cybersecurity assessment
Cybersecurity assessment should be carried out at every moment of application development - from the moment of creation of MVP, test version of the app to the finally implemented digital product and maintenance activities. Cybersecurity check focuses on writing security protocols and checklists, introducing code writing standards, firewalls, risk management and long-term protection strategy.
You should ensure that web application security assessment is carried out regularly (manually or automatically). And when a vulnerability is detected, ensure immediate response and make the necessary repairs.
5) Servers and IT systems
Keeping up to date versions of web servers, operating systems, content management systems (CMS), libraries and other software used for daily tasks. Try to install as many plugins/software/programs as necessary, because each one is a new hacker attack vector.
Follow the principle here: less is safer. Use firewalls to filter network traffic; enter the default blocking policy to reduce the likelihood of unauthorized traffic. Hide information about e.g. the version of the web server, mail server, filed server or SSH protocol used.
Regularity is the key to be seucre!
It is not surprising that only a systematic and consistent approach to business security and information can prevent a potential hacker attack on a company. After reading this article, ask your cybersecurity specialist when was the last time s/he analyzed the security of web applications. Ask also whether they meet the top 10 OWASP recommendations.
If s/he confirms that everything is under control and the applications are constantly verified, you can sleep peacefully (or rather with a slightly open eye). But if s/he suddenly fell silent, then let go of your sleep and immediately take on the security strategy in your company.








Let's stay in contact